
The Challenges of RPKI-ROA Diffusion in Research and Education
The ARIN 52 Public Policy and Members Meeting, held 19-20 October 2023 in San Diego, California, and online, began with an insightful keynote address titled “The Challenges of RPKI-ROA Diffusion Within the U.S. Research and Education Community.” Delivered by Internet2’s Director of Routing Integrity, Steve Wallace, this presentation shed light on the complexities surrounding Resource Public Key Infrastructure (RPKI) adoption in Internet2’s community of higher education, research institutions, government entities, corporations, and cultural organizations. Read on for a recap of this keynote and the critical issues, barriers, and potential solutions discussed.
Watch the recording of Steve Wallace’s keynote address on YouTube.
The Easy Button
Steve, whose role at Internet2 is to promote routing security and improve the routing security posture of their community, opened his keynote by sharing his “elevator pitch” for RPKI. Assuming a basic knowledge of RPKI and the creation of Route Origin Authorizations (ROAs), Steve explained how he refers to them as the “routing security easy button.” ROAs, created through a short and simple web form, serve as a powerful tool for mitigating network outages due to misconfigurations and certain hijack attempts. Emphasizing the ease of creating ROAs, Steve stressed that “everyone should be doing it.”
The Global Perspective
Steve then delved into a global perspective on RPKI and ROA adoption, presenting a graph comparing ROA coverage in the global Internet versus in U.S. research and education (R&E). “This is the kind of data I look at to motivate me,” he said. “I also share this data with our community to motivate them.”
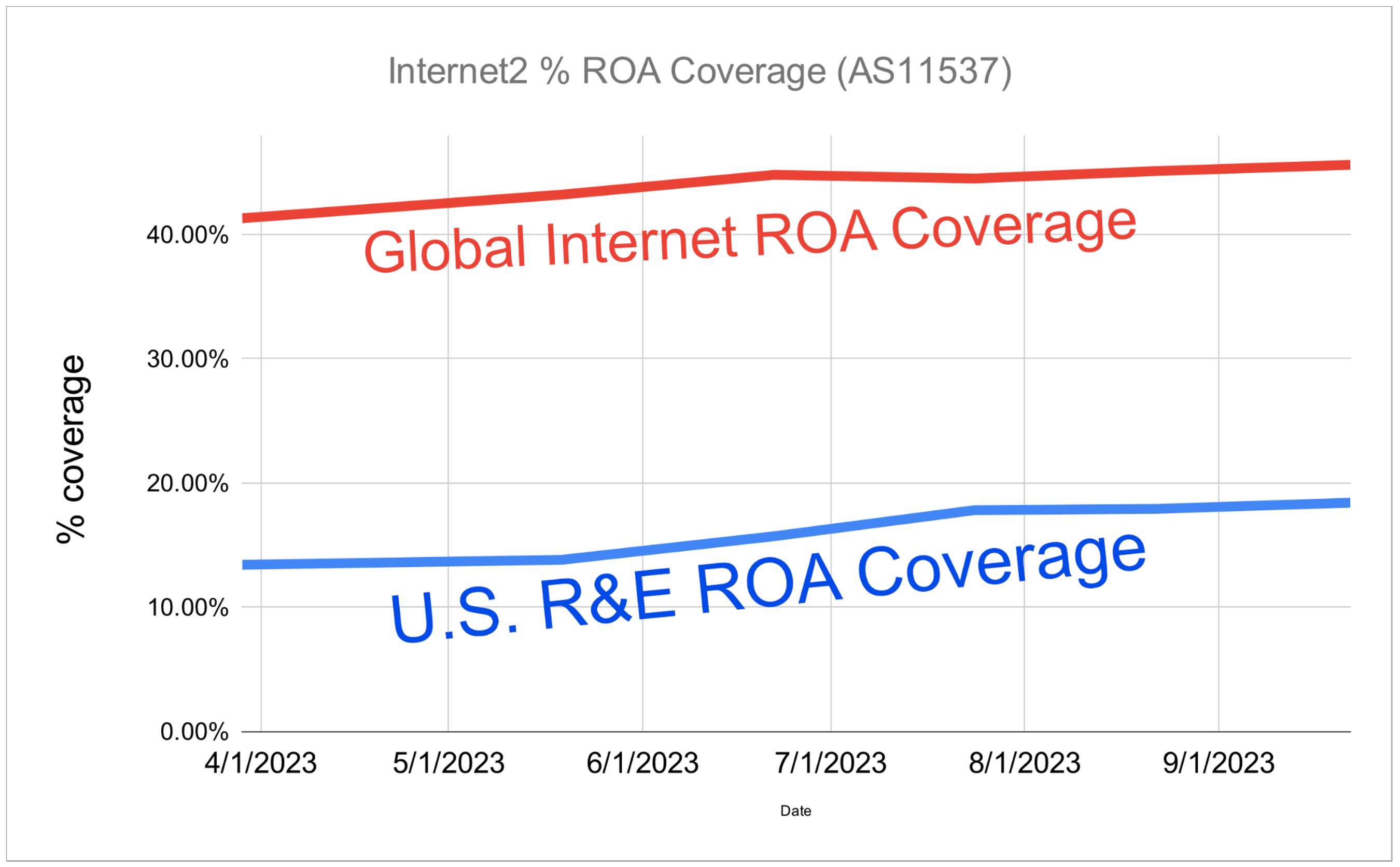
Noting that approximately 46 percent of routes in the global table have covering ROAs today, Steve explained how that represents a significant success story. Over the past five years, this coverage rate experienced a remarkable 35 percent year-over-year growth to jump from 10 to 46 percent. However, he pointed out that the U.S. R&E community lags significantly behind this global trend, with only 15-18 percent of prefixes being covered by ROAs.
The U.S. Research and Education Community
Before exploring the causes of this lag in the R&E community, Steve first explained what R&E networking entails. Internet2 is a nonprofit organization responsible for operating the national research and education network (NREN) in the U.S. It connects 46 regional and state networks, through which it serves organizations in all 50 states: More than 330 research universities and tens of thousands of Community Anchor Institutions. Steve clarified that Internet2 doesn’t provide full transit, so all those regional and state networks or the campuses themselves have full transit providers.
Internet2 also interconnects with 70 NRENs representing more than 100 countries around the world, and it isn’t the only one experiencing slow RPKI adoption. About a 20 percent of the global NREN routing table has ROA coverage — slightly higher than the U.S. R&E community on its own — but still less than half that of the global Internet.
MANRS and the IRR
Steve noted that a considerable portion of the Internet2 community participates in the Mutually Agreed Norms for Routing Security (MANRS) initiative, signaling their relatively strong interest in routing security. However, even within this group, the percentage of routes with covering ROAs fell short of the global Internet standard, raising questions about the remaining barriers to RPKI adoption.
When it comes to Internet Routing Registry (IRR) records, Internet2 recently experienced a very successful boost in participation within its community. When Google announced it would stop accepting routes without good IRR information for settlement-free peerings like the one Internet2 uses to provide high-speed access to cloud providers, IRR coverage jumped from about 60 percent of routes to more than 95 percent of routes. Steve’s investigation of why — if creating the IRR records themselves is no more difficult than creating a ROA — they were so successful in this situation but are still having difficulties with ROAs kicked off his list of barriers to RPKI-ROA adoption.
Barriers to RPKI-ROA Adoption
Technical Burden
While the responsibility for creating and maintaining IRR records can be shared by the IP address holder with their state or regional network, Steve described how RPKI-Route Origin Validation (ROV) transfers some of the technical burden for routing security from the Internet Service Provider (ISP) to the IP address holder. This works for well-resourced IP address holders (e.g., cloud providers, ISPs, etc.) but not for K-12 school districts, community colleges, and even some universities that lack the resources to shoulder that burden.
The Burden of Routing Security Controls
| Control | Origin Network | Transit Network |
|---|---|---|
| Filter Routes From Customer | ✓ | |
| Publish policy via IRR | ✓ | ✓ |
| Publish policy via auth-IRR | ✓ | |
| Publish RPKI-ROA | ✓ | |
| Publish ASPA | ✓ | |
| Publish origin router cert (BGPsec) | ✓ |
Legacy Resources
The Internet2 community comprises mostly early adopters of the Internet; more than 80 percent of the IP address assignments are legacy resources. More than 45 percent are legacy resources not covered by an ARIN Registration Services Agreement (RSA); an RSA is required to access ARIN’s advanced services like RPKI.
Learn about the options available to legacy resource holders at ARIN.
Navigating the ARIN Agreement
Most of the institutions Internet2 connects are public institutions, which frequently are subject to local law requiring changes to the RSA. Steve commended ARIN for significantly improving the agreement and the process for making changes and for accommodating changes for public institutions.
However, while ARIN provides clear instructions and policies for requesting and approving changes, the process still generates friction due to the technical and legal aspects involved. Network engineers must be convinced of the value of this new security feature (RPKI), and then leadership must be convinced of the value of allocating an attorney to go back and forth.
Myths About the RSA
Steve highlighted some misconceptions he has encountered regarding signing ARIN agreements, such as the fear that ARIN might reclaim IP addresses if they’re not efficiently used and the belief that it hinders IP address monetization — neither of which is the case.
He also applauded ARIN for recent user interface and reporting updates that have made it vastly easier to address the frequent lack of clarity about if an organization’s resources are covered by an RSA or not. In many cases, institutions in the Internet2 community do have some of their IP addresses or Autonomous System Numbers (ASNs) under an RSA, but they assume that the bills they receive and the resources they see in ARIN Online mean that all their resources are covered. ARIN Online now clearly indicates which resources are and are not covered, and ARIN publishes a daily Resources Under Registration Services Agreement (RSA) Report that lists each organization and whether they are receiving the full suite of ARIN’s registry services (meaning the resources are under agreement) or basic legacy services (meaning the resources are not under agreement).
“ARIN has worked with Internet2 to help us understand who in our community doesn’t have the agreements,” Steve said. “And that’s been very valuable because we can reach out to those people with a high degree of certainty and be able to tell them the status of those agreements and what that means. Now that ARIN is publishing that information, I think there’s an opportunity for other Internet service providers to use that information to inform their outreach to their customers.”
No Natural Champion
While “Chief Information Security Officer” (CISO) refers to “security,” Steve shared that in his experience CISOs and security teams have not yet integrated routing security into their organizations’ standards of cybersecurity care, instead seeing it as the network team’s responsibility.
“I think it’s important to change that, and I see some of that change happening,” Steve said. “And I think that will be a tipping point when that happens — when enough CISOs get in a room and they’re talking about routing security. But that’s not happened yet.”
Steve also pointed to confusion about who takes care of the range of security functions related to a network as part of this issue. Some networks within the Internet2 community outsource things like DDoS detection and mitigation, but they assume that routing security is included in that outsourcing as well and therefore already taken care of. But the reality is that routing security is its own domain and requires its own attention — across multiple teams in an organization.
Lack of Urgency
Without compelling deadlines — like the one that existed for creating IRR records with Google’s policy on settlement-free peerings — or incentives like a current outage or experiencing a route leak, there is little motivation among organizations to adopt RPKI and create ROAs.
Steve addressed the 31 December 2023 expiration of ARIN’s legacy fee cap, explaining that the impending pricing changes for legacy resources may create some urgency for small institutions. However, larger institutions with larger budgets may not be as impacted or motivated by the changes. Either way, this motivating factor will no longer be in play come 1 January 2024.
“ARIN’s sunsetting of the legacy fees has been helpful,” Steve said. “But we’re going to lose some momentum starting next year.”
Leadership Awareness
Closing out his list of barriers to RPKI adoption and ROA creation, Steve surmised that leadership is not hearing the message about the importance of routing security from the right avenues or the right number of avenues to drive it home and make it the standard of care it should be.
Addressing the Challenges
Steve then went on to share how Internet2 is working to overcome all those challenges:
- Extensive Outreach: Internet2 dedicates Steve’s full-time position to educating and raising awareness among leaders, decision-makers, and engineers in its community.
- Education and Support: Webinars, office hours, ROA-thons, and individual support sessions are offered to help organizations learn everything from “What is ARIN?” to how to create a ROA.
- Motivating Messaging: Steve emphasized the importance of getting organizations to recognize their Internet connection as critical infrastructure. That opens the door to convincing them of the need to create ROAs so that critical infrastructure can be protected and capable to the greatest extent possible now and in the future. Steve also encouraged transit providers with ROV to let their users know they can benefit from creating ROAs.
- Collaboration with ARIN: To address the friction experienced by public institutions, Internet2 continues to work with ARIN to streamline the ARIN agreement process.
- Encouraging Outsourcing: Organizations can delegate a Routing Point of Contact in their ARIN Online account to empower another party to create and maintain their ROAs. Steve reported that, although the process of designating a Routing Point of Contact isn’t streamlined, Internet2 is seeing instances of this, with some state and regional networks offering to manage those tasks on behalf of institutions who can’t or don’t want to deal with it themselves. He expressed the desire for ISPs who are willing to take this on to have an onboarding process to make the designation part of it easier for the customer.
Progress and Future Perspectives
Despite the challenges, progress has been made in RPKI adoption within the U.S. research and education community.
“As of three or four weeks ago, we’ve gotten [the] 700 number down to 600,” Steve said of the Internet2 organizations without an ARIN agreement.
“When I first started looking at this, ROA coverage was about 4 percent. Now it’s about 15 to 18 percent,” he reiterated. “[We’re] definitely increasing routing security; you have to give hats off to MANRS. I think they’ve done an excellent job making that something people are aware of.”
However, Steve expressed concerns about the lack of a similar centralized effort in other sectors. He suggested that Information Sharing and Analysis Centers (ISACs) or trade groups take up the cause of prioritizing and promoting routing security as an essential component of cybersecurity to the small organizations in their sectors.
Comments, Questions, and Conclusion
During the Q&A session that followed Steve’s presentation, ARIN community members added their thoughts on how to continue improving RPKI adoption numbers. The need for all address blocks owned by an organization to be given the capability of ROA management by a third party was noted as a barrier to delegating that responsibility, especially for organizations with large address blocks being leased out. It was also suggested that the messaging to promote RPKI should no longer be that it’s simply a nice add-on for routing security, but that it is becoming a basic connectivity requirement as cloud providers, transit providers, DDoS mitigation providers, and more are now making RPKI a prerequisite to use their services. Encouragement to use the ARIN Consultation and Suggestion Process (ACSP) to propose minor tweaks and improvements related to RPKI was offered, as was support for the integration of RPKI-related content into the Certified Information Systems Security Professional (CISSP) certification.
Steve Wallace’s keynote address at ARIN 52 shed light on the challenges and barriers faced by the U.S. R&E community in adopting RPKI and creating ROAs. By identifying these hurdles and proposing solutions, Internet2 is working toward a more secure and resilient Internet infrastructure within its own community and beyond. The comments provided by other ARIN community members added valuable insights and feedback on the topic of RPKI adoption and its significance in improving Internet security and connectivity.
To learn more about RPKI and ARIN’s routing security services, view our Resource Management Services guide.
Recent blogs categorized under: RPKI
GET THE LATEST!
Sign up to receive the latest news about ARIN and the most pressing issues facing the Internet community.
SIGN ME UP →Blog Categories
ARIN Bits • Tips • Updates • Elections • Caribbean • Outreach • Security • RPKI • Public Policy • Guest Post • Grant Program • Fellowship Program • Data Accuracy • IPv6 • Business Case for IPv6 • Internet Governance • Training • IPv4 • Customer Feedback • IRR


