
Turning Bits into Bites [Archived]
OUT OF DATE?
Here in the Vault, information is published in its final form and then not changed or updated. As a result, some content, specifically links to other pages and other references, may be out-of-date or no longer available.
I can has IPv6? Mathew Newton knows how to make IPv6 fun – by involving cats of course. Here’s how he connected a DIY device to the Internet of Things to solve a problem and make his feline friends extra happy on World IPv6 Day.
If we are to believe the figures being banded around, the Internet looks set to be dominated by the number of devices connecting under the ‘Internet of Things’ banner at some point over the coming years. If there’s any domination of the Internet before then it is arguably by cats – cat photos, cat videos, pretty much cat anything. I actually think there’s room for both though in the form of Internet-enabled cat feeders…
Back in 2009 I was looking for a solution to ensure our two cats didn’t go hungry if my wife and I had to work late or go out for the evening straight from work. I couldn’t help but feel that I already had half the solution by virtue of my home-grown security solution based around the use of IP cameras. We could see the cats via the Internet wherever we were, so why not feed them this way on an occasional basis also? Cutting a long story short (the full details of which can be found on my website with the obligatory cat video on YouTube) I built the first version (the ‘Mark 1’) of my cat feeder:

Aesthetics didn’t feature on the requirements list (well, not mine anyway – it turns out they did on my wife’s!) but function and reliability definitely did. It seemed to tick both of these boxes completely with little room for improvement.
That’s not to say my work was done however – I had to do something about the Cisco _Cat_alyst switch (I know, pun intended; it was clearly meant to be!) which I’d used to interface the feeder to the network through some hacked-together RJ45 loopback adapters and piggybacking on the port status LED driver ICs. Not only was the switch noisy but also bulky and had to be tethered to a nearby network port. After rummaging through piles of kits that ‘may come in handy one day’ I found a Cisco-Linksys WRT54GL broadband router and used it to make the improved ‘Mark 2’ version:

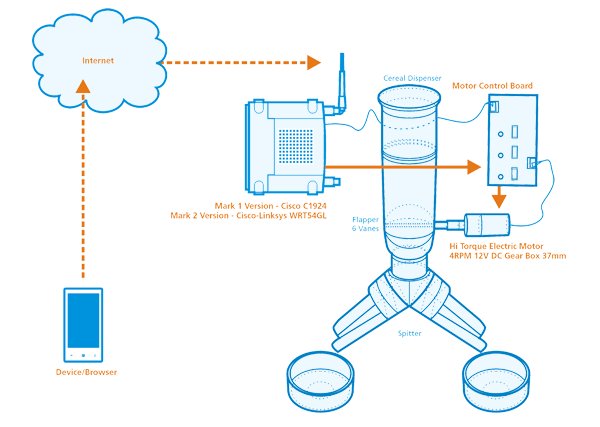
Not only was the feeder now a self-contained device, but it was also wireless (well, apart from the main power) and, by reflashing the firmware, could also support IPv6! The immediate benefit of this was, of course, being able to assign an appropriate ‘vanity’ address involving ::f00d and ::feed and no doubt others! Once that novelty wore off, the other benefits became obvious – there was no messing about with port forwarding and dynamic DNS update scripts. It just worked. Out of the box. This could of course be a double-edged sword where network security relies solely on the stateful property of a NAT and so my first IoT lesson to learn was making sure that my firewall was configured to protect the feeder accordingly.
The second lesson was also security-themed, and I’ve only got myself to blame for this one. On World IPv6 Day in June 2011, I decided to open up the feeder for 24 hours for anyone to access. For those connecting over IPv4 they could only view the feeder-mounted webcams, but for those with IPv6 they could also take control of the feeder and feed the cats. You can probably imagine how it went – food pretty much everywhere and two very full cats! The real problem, however, was that some users had spotted that I was passing control parameters through the URL to a PHP script (e.g. /catfeedercontrol.php?action=feed&time=5) and so were trying to abuse this by manipulating the feed durations, fishing for other commands and goodness knows what else. I quickly added some sanity checking to the scripts to mitigate this (I didn’t do this previously because access was usually password controlled). A key point to note here is that this attack vector was not directly related to the use of IPv6 as such – the vulnerability was at the application layer after all – however the ease with which IPv6 allows devices to be reachable from the Internet highlights the importance of ensuring that security is properly considered at all layers of the stack.
Even with sanity checking I would have benefited from being able to rate limit access but didn’t have time to work out how to do this. Instead, I opted to filter the source address of repeat offenders using the firewall and this became my third security lesson. The IPv6 double-edge sword was back – the offender was either hopping between addresses (whether that be manually or using short-term privacy addresses) or an entire organisation was seemingly in on the act because the addresses were all over the place within a very large prefix! I assumed the former but given the futility of playing cat and mouse with the offender (pun not intended!) I gave up blocking individual addresses and filtered the entire prefix instead. In a ‘real world’ application this could of course have significant unintended consequences, and so it did make me realise that our approach to filter-by-address strategies in IPv4 might need further thought when it comes to IPv6.
All in all, the cat feeder has been a great success and has never let us down in the six years we’ve been using it (I should point out that we only use it on occasion and not as a substitute for in-person contact with our pets!). Indeed, the cats seem to love it although it has to be said they’d love anything that feeds them! I suspect though that they might be particularly keen on the IPv6 aspect as normally they are fed twice a day but on World IPv6 Day they were fed a total of 168 meals. So from their perspective, this answers the question as to how much better IPv6 is than IPv4… 84 times of course!
 Mathew has nearly 20 years of network-related experience with a particular focus on all aspects relating to the design and deployment of IP (v4 and v6) and DNS.
Mathew has nearly 20 years of network-related experience with a particular focus on all aspects relating to the design and deployment of IP (v4 and v6) and DNS.
His interest in computing, electronics and ‘how things work’ arguably stems from a childhood of taking things apart. He is now at the level where hardly any screws are left over when putting them back together again.
Any views, positions, statements or opinions of a guest blog post are those of the author alone and do not represent those of ARIN. ARIN does not guarantee the accuracy, completeness or validity of any claims or statements, nor shall ARIN be liable for any representations, omissions or errors contained in a guest blog post.
OUT OF DATE?
Here in the Vault, information is published in its final form and then not changed or updated. As a result, some content, specifically links to other pages and other references, may be out-of-date or no longer available.
